CSS Question Paper solution Dec 2023 – Part 2
Table of Contents
Q3 a. List the functions of the different protocols of SSL. Explain the handshake protocol. 10
THIS ANSWER IS AN CHATGPT GENERATED ANSWER
Functions of SSL/TLS Protocols:
- Record Protocol:
- Responsible for encapsulating higher-level protocol data for secure transmission over the network.
- Handles fragmentation and reassembly of messages.
- Provides data confidentiality, integrity, and authentication through encryption, message authentication codes (MACs), and optional compression.
- Handshake Protocol:
- Establishes a secure connection between the client and server.
- Negotiates encryption algorithms, cryptographic keys, and session parameters.
- Authenticates the server to the client and optionally vice versa.
- Facilitates the exchange of cryptographic parameters necessary for secure communication.
- Change Cipher Spec Protocol:
- Signals the transition to encrypted communication.
- Indicates that subsequent records will be protected using negotiated cryptographic algorithms and keys.
- Ensures that both parties switch to the agreed-upon security parameters simultaneously.
- Alert Protocol:
- Handles error messages and alerts between the client and server.
- Notifies parties about unexpected or abnormal conditions, such as handshake failures, decryption errors, or certificate issues.
- Allows graceful termination of connections in case of errors or security breaches.
Handshake Protocol:
The handshake protocol is a critical component of SSL/TLS, responsible for initiating a secure connection between a client and a server. It consists of a series of steps:
- ClientHello:
- The client initiates the handshake by sending a ClientHello message to the server.
- Contains cryptographic parameters supported by the client, such as supported cipher suites, SSL/TLS version, and random data.
- ServerHello:
- The server responds to the ClientHello with a ServerHello message.
- Selects the highest SSL/TLS version and cipher suite supported by both the client and server.
- Optionally includes the server’s digital certificate for authentication.
- Server Certificate (optional):
- If the server requires client authentication, it sends its digital certificate to the client.
- The client verifies the authenticity of the server’s certificate using its trust store and the configured validation rules.
- Key Exchange:
- The server and client perform key exchange to establish shared secret keys for encryption and authentication.
- Key exchange methods vary based on the chosen cipher suite, such as RSA, Diffie-Hellman, or elliptic curve cryptography.
- Finished Messages:
- Both the client and server send Finished messages to confirm that the handshake is complete.
- These messages contain a hash of all preceding handshake messages, providing integrity protection for the handshake process.
Q3 b. List different poly-alphabetic substitution ciphers. Encrypt “The key is hidden under the door” using playfair cipher with keyword “domestic”. 10
List of ciphers – https://www.apprendre-en-ligne.net/crypto/bibliotheque/Plotz/Doc/CipherList.html
You can use playfair cipher calculator to check your answers
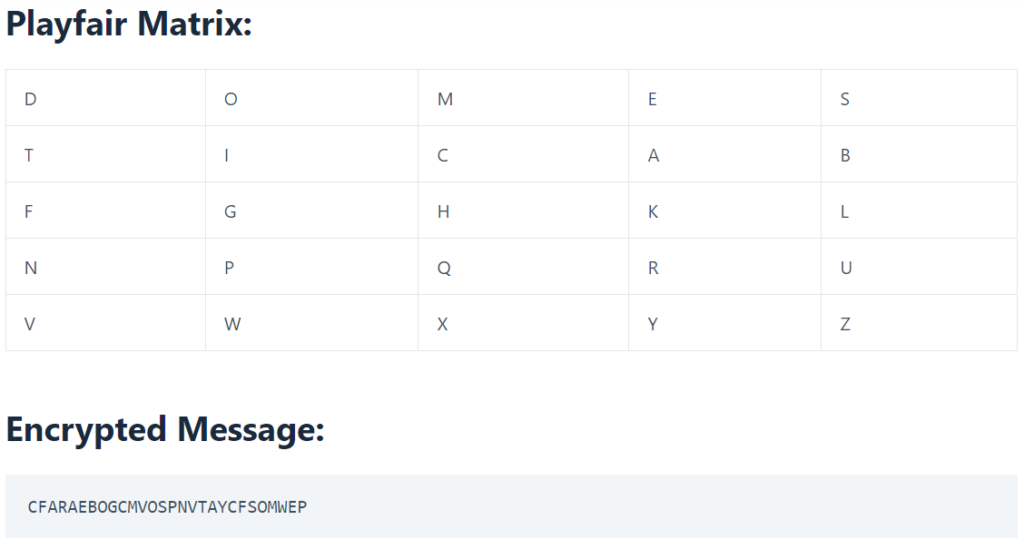
answer for numerical here : https://www.doubtly.in/q/encrypt-key-hidden-door-playfair-cipher-keyword-domestic/
Q4. a. Define digital signature. Explain any digital signature algorithm in detail. 10
The Digital Signature Algorithm (DSA) is a cryptographic algorithm that is used to generate and verify digital signatures. It was developed in the United States by the National Institute of Standards and Technology. DSA allows recipients to authenticate the sender’s identity by verifying the signature using their public key. It also ensures integrity, as any modification to the message will render the signature invalid, allowing recipients to detect tampering.
DSA has been widely adopted and used in various applications, including secure email, digital certificates, and secure electronic transactions.
Read more : https://www.ques10.com/p/18988/explain-any-one-digital-signature-algorithm-in-d-1/
Q4 b. Give the format of X.509 digital certificate and explain the use of a digital signature in it. 10
Answer here : https://www.doubtly.in/q/give-format-509-digital-certificate-explain-digital-signature/
Q5 a. Explain session hijacking and management. 10
Session Hijacking is a Hacking Technique. In this, the hackers (the one who perform hacking) gain the access of a target’s computer or online account and exploit the whole web session control mechanism. This is done by taking over an active TCP/IP communication session by performing illegal actions on a protected network. Normally, the web sessions are managed by the session token. The Session Hijacker has access over everything which the actual user has. For Example, shopping in an online store or paying your electricity bills, the session hijackers attack over web browsers or web application sessions.
To perform these all kinds of Session Hijacking attacks, the attackers use various methods. They have the choice to use a single method or more than one method simultaneously to perform Session Hijacking. Those methods are:
- Brute-forcing the Session ID
- Cross-Site Scripting (XSS) or Misdirected Trust
- Man-in-the-browser
- Malware infections
- Session Fixation
- Session side-jacking
Session management is the process of securely managing user sessions to prevent unauthorized access and session hijacking. Here are some best practices for session management to mitigate the risk of session hijacking:
- Use Secure Session Tokens: Generate session tokens that are long, random, and unpredictable. Use secure mechanisms for generating and transmitting session tokens, such as using HTTPS and secure cookies with the ‘HttpOnly’ and ‘Secure’ flags.
- Implement Session Expiry: Set a reasonable session timeout period to limit the duration of active sessions. When sessions expire, users must re-authenticate, reducing the window of opportunity for attackers to hijack sessions.
- Protect Session Data: Encrypt sensitive session data, both in transit and at rest, to prevent eavesdropping and unauthorized access. Avoid storing sensitive information in client-side storage mechanisms like cookies unless absolutely necessary.
- Use Anti-CSRF Tokens: Implement anti-CSRF (Cross-Site Request Forgery) tokens to prevent CSRF attacks, which can be used in conjunction with session hijacking to carry out unauthorized actions.
- Monitor Session Activity: Monitor session activity for anomalies, such as multiple concurrent sessions from different IP addresses or unusual user behavior, which could indicate a session hijacking attempt.
- Educate Users: Educate users about the risks of session hijacking and how to recognize phishing attempts and other social engineering tactics used by attackers to steal session identifiers.
Q5 b. What is need of Diffie-Hellman algorithm. User A and B decide to use Diffie-Hellman algorithm to share a key. They choose p = 23 and g = 5 as the public parameters. Their secret keys are 6 and 15 respectively. Compute the secret key that they share. 10
Answer : https://www.doubtly.in/q/user-decide-diffie-hellman-algorithm-share-key/
Q6. Attempt any Four.
a. Explain the different types of firewalls and mention the layer in which they operate. 05
- Packet Filters:
- Layer: Network Layer (Layer 3)
- These firewalls control network access by examining individual packets of data and making decisions based on source/destination IP addresses, protocols, and ports.
- Stateful Inspection Firewalls:
- Layer: Network and Transport Layers (Layer 3 and Layer 4)
- They monitor the state of active connections and permit communication only if a valid session is established between endpoints.
- Application Layer Firewalls:
- Layer: Application Layer (Layer 7)
- These firewalls analyze application-layer information, such as HTTP requests, to detect and block suspicious activities.
- Next-generation Firewalls:
- Layer: Varies, often multiple layers
- They incorporate advanced features like application awareness, intrusion prevention, and cloud-delivered threat intelligence, offering enhanced security compared to traditional firewalls.
- Circuit-level Gateways:
- Layer: Session Layer (Layer 5) and Application Layer (Layer 7)
- These firewalls provide security at the transport and application layers, offering TCP and UDP connection security.
- Software Firewalls:
- These are software applications installed on computers to protect against external threats by notifying users about potential risks, such as opening insecure emails or websites.
- Hardware Firewalls:
- These physical appliances enforce network boundaries, inspecting both inbound and outbound traffic to enforce access controls and security policies.
- Cloud Firewalls:
- These are software-based, cloud-deployed network devices that protect private networks from unauthorized access by filtering data at the cloud level.
b. List and explain vulnerabilities in windows operating system. 05
Answer : https://www.doubtly.in/q/list-explain-vulnerabilities-windows-operating-system/
c. List and explain characteristics needed in secure hash function. 05
Answer here : https://www.doubtly.in/q/list-explain-characteristics-needed-secure-hash-function/
d. Explain Triple DES in short. 05
The speed of exhaustive key searches against DES after 1990 began to cause discomfort amongst users of DES. However, users did not want to replace DES as it takes an enormous amount of time and money to change encryption algorithms that are widely adopted and embedded in large security architectures.
The pragmatic approach was not to abandon the DES completely, but to change the manner in which DES is used. This led to the modified schemes of Triple DES (sometimes known as 3DES).
Incidentally, there are two variants of Triple DES known as 3-key Triple DES (3TDES) and 2-key Triple DES (2TDES).
3-KEY Triple DES
Before using 3TDES, user first generate and distribute a 3TDES key K, which consists of three different DES keys K1, K2 and K3. This means that the actual 3TDES key has length 3×56 = 168 bits. The encryption scheme is illustrated as follows −
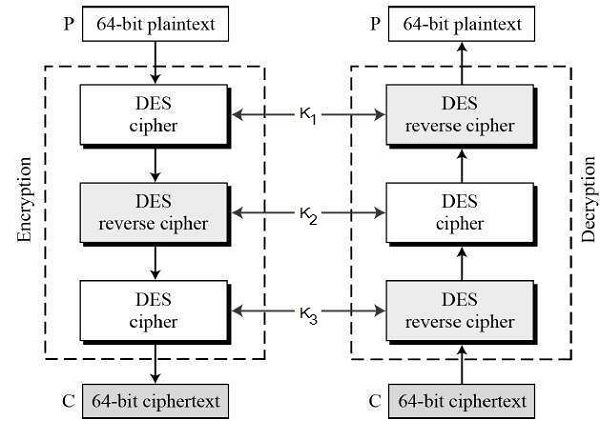
The encryption-decryption process is as follows −
- Encrypt the plaintext blocks using single DES with key K1.
- Now decrypt the output of step 1 using single DES with key K2.
- Finally, encrypt the output of step 2 using single DES with key K3.
- The output of step 3 is the ciphertext.
- Decryption of a ciphertext is a reverse process. User first decrypt using K3, then encrypt with K2, and finally decrypt with K1.
Due to this design of Triple DES as an encrypt–decrypt–encrypt process, it is possible to use a 3TDES (hardware) implementation for single DES by setting K1, K2, and K3 to be the same value. This provides backwards compatibility with DES.
Second variant of Triple DES (2TDES) is identical to 3TDES except that K3is replaced by K1. In other words, user encrypt plaintext blocks with key K1, then decrypt with key K2, and finally encrypt with K1 again. Therefore, 2TDES has a key length of 112 bits.
Triple DES systems are significantly more secure than single DES, but these are clearly a much slower process than encryption using single DES.
Src : https://www.tutorialspoint.com/cryptography/triple_des.htm
e. Explain with examples, keyed and keyless transposition ciphers. 05 [repeated]
Transposition Cipher:
A transposition cipher does not substitute one symbol for another (as in substitution cipher), but changes the location of these symbols. It reorders (jumbles) the given plain-text to give the cipher-text. They are of two types: Keyed and Keyless Transposition Cipher.
Keyless Transposition Cipher:
In this cipher technique, the message is converted to ciphertext by either of two permutation techniques:
a. Text is written into a table column-by-column and is then transmitted row-by-row.
b. Text is written into a table row-by-row and is then transmitted column-by-column
The first method (a) is also popularly known as Rail-fence cipher
E.g. We need to send the message “DEFENDTHEEASTWALL”. Arranging into tables we get :
Now, the message is sent row-by-row. So Ciphertext is “DFNTEATALEEDHESWL”(Note: the no. of rows is 2 by default, unless specified)
Similarly for the (b) method, we can arrange the same above message into tables with four columns.
The Data is then transmitted column-by-column as “DNETLEDEWFTAAEHSL”
Keyed Transposition cipher:
In this approach, rather than permuting all the symbols together, we divide the entire plaintext into blocks of predetermined size and then permute each block independently.
Suppose A wants to send a message to B “WE HAVE AN ATTACK”. Both A and B agreed to had previously agreed oved the blocks size as 5. So the blocks would be as:
The last character X is a bogus character so as to complete the block size of 5.
A and B is using the following key for encryption and decryption:
