Computer Network Question paper Solutions (AI-DS/AI-ML/CSE(DS/AIML))
Computer Network Question paper december 2022

Q1) a) Compare and contrast Circuit switched network and Packet switched network
A comparison of circuit switched and packet-switched networks
Q1)b) Describe the different guided transmission medias used in the network.
GUIDED TRANSMISSION MEDIA
The physical layer is to transport bits from one machine to another. Various physical media can be used for the actual transmission.
- • Magnetic Media
- • Twisted Pair
- • Coaxial Cable
- • Fiber Optics
Magnetic Media :
Magnetic tape or removable media (e.g., recordable DVDs), physically transport the tape or disks to the destination machine, and read them back in again. This method is more cost effective, especially for applications in which high bandwidth or cost per bit transported is the key factor.
Twisted Pairs :
Magnetic tape has poor delay characteristics. Transmission time is measured in minutes or hours, not milliseconds. A twisted pair consists of two insulated copper wires, typically about 1 mm thick. The wires are twisted together in a helical form. Twisting is done because two parallel wires constitute a fine antenna. When the wires are twisted, the waves from different twists cancel out, so the wire radiates less effectively. A signal is usually carried as the difference in voltage between the two wires in the pair. Provides better immunity to external noise. Used for transmitting either analog or digital information .
Twisted Pairs : Twisted-pair cabling comes in several varieties. The garden variety deployed in many office buildings is called Category 5 cabling, or ‘‘Cat 5’’. A category 5 twisted pair consists of two insulated wires gently twisted together. Four such pairs are typically grouped in a plastic sheath to protect the wires and keep them together. Different LAN standards may use the twisted pairs differently. For example, 100-Mbps Ethernet uses two (out of the four) pairs, one pair for each direction.
Coaxial Cable :
• It has better shielding and greater bandwidth than unshielded twisted pairs, so it can span longer distances at higher speeds. • Two kinds of coaxial cable are widely used. 50-ohm cable is commonly used when it is intended for digital transmission from the start. 75-ohm cable is commonly used for analog transmission and cable television
Fiber Optics :
Fiber optics are used for long-haul transmission in network backbones, highspeed LANs, and high-speed Internet access such as FttH (Fiber to the Home). • An optical transmission system has three key components: the light source, the transmission medium, and the detector. • A pulse of light indicates a 1 bit and the absence of light indicates a 0 bit. • The transmission medium is an ultra-thin fiber of glass. The detector generates an electrical pulse when light falls on it. • Connects a light source to one end of an optical fiber and a detector to the other. There is a unidirectional data transmission system that accepts an electrical signal, converts and transmits it by light pulses, and then reconverts the output to an electrical signal at the receiving end.
Q1)c) What is Channel Allocation problem? Explain in short pure and slotted ALOHA.
The Channel Allocation problem refers to the challenge of efficiently allocating a shared communication channel, such as a radio frequency or a time slot, among multiple users or devices to minimize interference and maximize the utilization of the channel. This problem is common in wireless communication systems and networks.
Pure ALOHA and Slotted ALOHA are two early multiple access protocols used to address the Channel Allocation problem:
- Pure ALOHA:
- In Pure ALOHA, devices transmit data frames whenever they have data to send, without any regard for the timing of other devices.
- Collisions can occur when two or more devices transmit simultaneously, leading to data frame corruption.
- Collided frames are typically detected through acknowledgments or by checking for collisions after transmission.
- After a collision, devices use random backoff times before attempting to retransmit their data.
- Pure ALOHA is inefficient because of its high collision rate, resulting in low channel utilization.
- Slotted ALOHA:
- Slotted ALOHA divides time into discrete slots, and devices are required to transmit data only at the beginning of a time slot.
- This synchronization reduces the chance of collisions because devices are less likely to overlap in their transmissions.
- Like Pure ALOHA, Slotted ALOHA also handles collisions by detecting them and initiating retransmissions.
- Slotted ALOHA is more efficient than Pure ALOHA in terms of channel utilization, but it still suffers from some inefficiencies, especially as the number of devices or the traffic load increases.
Q1) d) Obtain the 4-bit CRC code for the data bit sequence 10011011100 using the polynomial x4 +x2 +1.
Final Code : 100110111001100
divisor : x4 +x2 +1 = x4 +x3+x2 +x+1 = 10101
n=5
no of bits to be added = n-1 = 5-1=4
divdend= 100110111000000

Q2)a) Describe in detail OSI reference model with a neat diagram
The OSI model is based on a proposal developed by the International Standards Organization (ISO) as a first step toward international standardization of the protocols used in the various layers (Day and Zimmermann, 1983). It was revised in 1995 (Day, 1995). The model is called the ISO OSI (Open Systems Interconnection) Reference Model because it deals with connecting open systems—that is, systems that are open for communication with other systems. The OSI model has seven layers
Here’s an overview of the seven layers of the OSI reference model, from the bottom (Layer 1) to the top (Layer 7):
- Physical Layer: This is the lowest layer and deals with the physical aspects of network communication, such as cables, connectors, and electrical voltages. It defines the hardware requirements for transmitting raw binary data over a physical medium.
- Data Link Layer: The Data Link Layer is responsible for establishing a reliable link between two directly connected nodes. It ensures data integrity, handles error detection and correction, and manages access to the physical medium. Ethernet and Wi-Fi protocols operate at this layer.
- Network Layer: The Network Layer is responsible for routing data packets from the source to the destination across multiple intermediate devices (routers). It deals with logical addressing (such as IP addresses), packet forwarding, and routing decisions. The Internet Protocol (IP) operates at this layer.
- Transport Layer: The Transport Layer manages end-to-end communication between devices and ensures data delivery, error checking, and flow control. It can establish connections (in the case of TCP) or provide a connectionless service (in the case of UDP).
- Session Layer: The Session Layer establishes, maintains, and terminates communication sessions between two devices. It handles functions like session synchronization, checkpointing, and recovery.
- Presentation Layer: The Presentation Layer is responsible for data translation, encryption, and compression. It ensures that data exchanged between devices is in a format that both can understand, regardless of differences in data representation or encoding.
- Application Layer: The Application Layer is the topmost layer and is closest to the end-user. It provides network services directly to applications and end-users, including functions like file transfer, email, web browsing, and remote access. Many different application protocols, such as HTTP (for web browsing) and SMTP (for email), operate at this layer.
Q2)b) What is Channel allocation problem? Explain CSMA/CD protocol. A network with CSMA/CD has 10 Mbps bandwidth and 25.6ms maximum propagation delay. What is the minimum frame size ?
https://www.doubtly.in/10777/channel-allocation-problem-explain-protocol-network-with-mbps-bandwidth
Q3 ) a) Compare and contrast between
i) IPv4 vs IPv6
| Feature | IPv4 | IPv6 |
|---|---|---|
| Address Length | 32 bits (approximately 4.3 billion addresses) | 128 bits (approximately 340 undecillion addresses) |
| Address Notation | Dotted-decimal (e.g., 192.168.1.1) | Hexadecimal with colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334) |
| Address Configuration | Manual or DHCP | Stateless autoconfiguration, DHCPv6 |
| Header Length | Variable (20 to 60 bytes) | Fixed at 40 bytes |
| Header Checksum | Included (recalculated at each hop) | Removed (reliant on link-layer checksum) |
| Security and Encryption | Requires additional IPsec layer | Built-in support for IPsec |
| NAT (Network Address Translation) | Commonly used | Discouraged due to abundant addresses |
| Backward Compatibility | Transition mechanisms like dual-stack and tunneling | Coexistence during transition period |
| Deployment Status | Widely used with address exhaustion issues | Increasing adoption for future scalability |
ii) Connection oriented protocol vs Connectionless protocol
| Feature | Connection-Oriented Protocol | Connectionless Protocol |
|---|---|---|
| Establishment of Connection | A dedicated connection is established before data transfer. | No dedicated connection is established; each packet is treated independently. |
| Reliability | High reliability, as it ensures data integrity and order. | Generally less reliable, as there is no guarantee of packet delivery or order. |
| Acknowledgment | Acknowledgments are used to confirm successful data packet delivery. | No acknowledgments are provided, and lost packets may not be retransmitted. |
| Sequential Data Transfer | Data is sent and received in a sequential manner, maintaining order. | Each packet is sent independently, and the order of arrival may vary. |
| Overhead | More overhead due to the establishment and maintenance of connections. | Less overhead, as there is no need to set up and tear down connections. |
| Example Protocol | TCP (Transmission Control Protocol) | UDP (User Datagram Protocol) |
Q3) b) Explain in brief Cisco PPDIOO Network design Methodology
PPDIOO is a network design methodology used by Cisco. It stands for Prepare, Plan, Design, Implement, Operate, and Optimize.
- Prepare:
- Defining network goals and requirements.
- Identifying key stakeholders.
- Establishing project scope.
- Plan:
- Creating a high-level network design.
- Specifying technologies, protocols, and services.
- Performing a gap analysis.
- Design:
- Developing detailed network design.
- Creating physical and logical network diagrams.
- Defining addressing schemes and selecting hardware/software.
- Implement:
- Procuring and configuring network equipment and software.
- Testing and verifying network functionality.
- Executing installation, configuration, and migration tasks.
- Operate:
- Managing day-to-day network operations.
- Monitoring network performance.
- Troubleshooting and ensuring security/compliance.
- Maintaining documentation and providing team training.
- Optimize:
- Continually improving network performance and efficiency.
- Conducting periodic assessments and analysis.
- Making necessary adjustments to meet evolving business needs.
Q 4 a) What is SDN? Explain SDN architecture along with Operations of control and data planes
Q4) b) What is Routing? What are desirable characteristics of routing algorithms? Explain distance vector routing with suitable example
Routing:
Routing is the process of determining the path that data packets should take from the source to the destination in a computer network. It involves making decisions about the optimal routes based on various metrics and network conditions. Routing is a critical aspect of network communication as it ensures efficient and reliable data transfer.
Desirable Characteristics of Routing Algorithms:
- Correctness: The routing algorithm should correctly determine the paths to destinations, ensuring that data reaches the intended recipients.
- Simplicity: Routing algorithms should be simple to understand, implement, and maintain to facilitate efficient network management.
- Robustness: The algorithm should be robust enough to handle changes in network topology, link failures, or other dynamic conditions.
- Scalability: Routing algorithms should scale effectively with the size of the network, supporting a growing number of nodes and links.
- Optimality: The algorithm should strive to find optimal paths based on predefined metrics, such as minimizing hop count, latency, or maximizing available bandwidth.
- Adaptability: The routing algorithm should adapt to changes in the network, adjusting routes dynamically in response to varying conditions.
Distance Vector Routing:
Distance Vector Routing is a type of routing algorithm where each node maintains a table (vector) that contains the distance (cost) to every other node in the network. The distance vector is periodically exchanged with neighboring nodes. A common distance vector algorithm is the Bellman-Ford algorithm.
Example:
Consider a small network with four nodes (A, B, C, D) and the following initial distance vector table for node A:
| Destination | Cost (A to Destination) |
|---|---|
| A | 0 |
| B | 1 |
| C | 3 |
| D | ∞ |
- In this table, the cost from A to A is 0, and the cost to B, C, and D is initially set to 1, 3, and infinity (∞), respectively.
- Node A periodically shares its distance vector with its neighbors (B, C, D).
- Upon receiving the distance vectors from its neighbors, A updates its own distance vector based on the received information and the known costs.
- This process repeats iteratively until convergence, with nodes updating their distance vectors and exchanging information until a consistent and stable routing table is achieved.
- The algorithm aims to minimize the cost to reach each destination and converge to a state where no further updates are needed.
Q 5 a) Elaborate the architectures of NOX and POX controllers of SDN with their comparison
Q5) b) Elaborate Cisco SONA Architecture in detail
The Cisco Service-Oriented Network Architecture (SONA) is a conceptual architecture that describes how to design networks to be more agile, efficient, and scalable.
SONA is based on the principles of service orientation, which means that the network is designed to provide services to applications rather than just providing connectivity. This means that the network is more flexible and can be more easily adapted to changing business needs.
SONA consists of three layers:
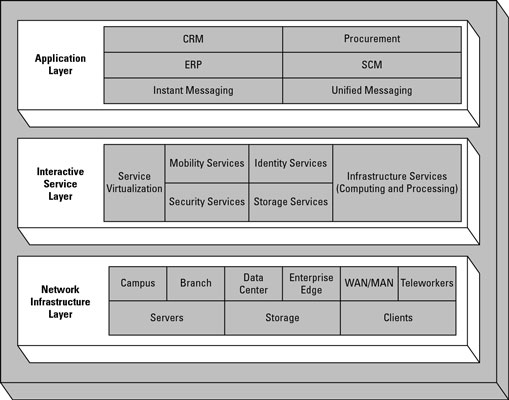
- The Network Infrastructure Layer: The Network Infrastructure Layer is the foundation of the SONA architecture. It provides the physical and virtual resources that are used to deliver network services. This layer is made up of the following components:
- Network devices: Network devices such as routers, switches, and firewalls are responsible for routing traffic, providing security, and other network functions.
- Servers: Servers are responsible for running applications and providing storage.
- Clients: Clients are the devices that users use to access the network, such as computers, laptops, and smartphones.
- The Interactive Services Layer: The Interactive Services Layer provides the network services that are used by applications. This layer is made up of the following components:
- Application services: Application services are the network services that are used by applications to perform specific tasks, such as security, mobility, and storage.
- Business services: Business services are the network services that are used by business processes to support their operations, such as customer relationship management (CRM) and supply chain management (SCM).
- Collaboration services: Collaboration services are the network services that are used by users to collaborate with each other, such as video conferencing and instant messaging.
- The Applications Layer: The Applications Layer is the top layer of the SONA architecture. It contains the applications that are used by users. Applications can be anything from web applications to mobile apps to desktop applications.
Q 6 Write a short note on
a) Sliding Window Protocol
https://www.doubtly.in/10640/write-short-note-on-sliding-window-protocol
b) OpenFlow messages
https://www.doubtly.in/10780/write-short-note-on-openflow-messages
c) NAT
Network Address Translation (NAT) is a crucial technology used in computer networks, especially within homes and businesses. It primarily serves two main purposes:
- Conserving IP Addresses: NAT allows multiple devices in a local network to share a single public IP address for accessing the internet. This is essential due to the limited availability of IPv4 addresses. It conserves these valuable public IP addresses by using a single address for several devices.
- Enhancing Security: NAT acts as a protective barrier between the local network and the internet. When devices in the local network communicate with the internet, NAT modifies the source IP address in the outgoing data packets to the public IP address. This means external entities on the internet see only the public IP address and not the individual local IP addresses of devices. In effect, it hides the structure of the internal network from potential threats.
NAT works by maintaining a translation table, which keeps track of which internal device corresponds to which external port number. When incoming data packets return from the internet to the NAT router, it uses this table to correctly route the data to the appropriate internal device.
d) DHCP
DHCP is a network protocol used to assign dynamic IP addresses and other network configuration settings to devices on a network. It simplifies network administration by automating the process of assigning IP addresses, subnet masks, gateway addresses, and other parameters. When a device connects to a network, DHCP ensures that it receives the necessary network settings, making it an essential component for the seamless operation of networks, both large and small.
Computer Network Question paper May 2023
Q.1 Solve any four
a) Explain principle differences between connection less and connection oriented communication. ( repeated from dec check answer above )
b) What is channel allocation problem? ( repeated from dec check answer above )
c) Find the error, if any, in the following IPv4 addresses. (i) 221.24.7.8.20 (ii) 75.45.351.14
There are errors in both of the provided IPv4 addresses:
(i) 221.24.7.8.20:
- The IPv4 address format consists of four octets separated by periods (dots). In this case, there are more than four octets.
- Corrected Format: 221.24.7.8
(ii) 75.45.351.14:
- Each octet in an IPv4 address must be a decimal number ranging from 0 to 255.
- The third octet “351” exceeds the valid range (0-255).
- Corrected Format: 75.45.255.14
In both cases, the corrected IPv4 addresses adhere to the standard format with four octets, each containing a valid decimal number between 0 and 255.
d) Differentiate between TCP and UDP.
| Feature | TCP | UDP |
|---|---|---|
| Connection Type | Connection-oriented | Connectionless |
| Reliability | Reliable: ensures data delivery | Unreliable: no guaranteed delivery |
| Acknowledgments | Yes (acknowledgment for each packet) | No acknowledgment of packet delivery |
| Order of Delivery | Yes (maintains order of sent packets) | No (order of delivery not guaranteed) |
| Flow Control | Yes (implements flow control to manage data transfer) | No (limited flow control, relies on the application) |
| Error Checking | Yes (error-checking through checksums) | Limited (optional checksum) |
| Header Size | Larger header size | Smaller header size |
| Transmission Speed | Slower than UDP due to connection setup | Faster than TCP due to no connection setup |
| Usage | Reliable data transfer (e.g., file transfer, web browsing) | Real-time applications (e.g., video streaming, online gaming) |
| Examples | HTTP, FTP, SMTP | DNS, DHCP, VoIP |
e) Write short note on SMTP.
SMTP, or Simple Mail Transfer Protocol, is a standard communication protocol used for sending and receiving electronic mail (email) on the internet. It is an essential part of the email delivery process, responsible for transferring outgoing emails from the sender’s mail server to the recipient’s mail server.
Key Features and Functions:
- Message Transfer:
- SMTP facilitates the transfer of emails between mail servers. When you send an email, your email client uses SMTP to communicate with your email provider’s server to transmit the message.
- Transmission Rules:
- SMTP follows a set of rules for the transmission of emails. These rules dictate how the email message should be formatted, the information required in the message headers, and the commands used for communication between servers.
- Communication Model:
- SMTP operates on a client-server model. The email client acts as the client, initiating communication with the server, which is responsible for sending or relaying the email.
- Port Number:
- SMTP typically uses port 25 for unencrypted communication. For secure communication, SMTP over TLS (SMTPS) uses port 587. SMTPS provides encryption through Transport Layer Security (TLS) to secure the email transmission.
- Authentication:
- SMTP servers may require authentication to ensure that only authorized users can send emails. Common authentication methods include username and password verification.
- Message Format:
- SMTP defines the structure of email messages, including the header and body format. The header contains information such as the sender, recipient, subject, and date, while the body contains the actual content of the email.
- Relaying:
- SMTP supports the relaying of emails through multiple servers. For example, if the recipient’s mail server is not directly reachable, intermediate servers can relay the email to its destination.
- Limitations:
- SMTP is primarily concerned with the transmission of emails and doesn’t handle tasks such as email storage or retrieval. Other protocols like POP3 (Post Office Protocol) and IMAP (Internet Message Access Protocol) are used for those purposes.
Example:
- When you send an email through your email client (e.g., Outlook, Gmail), the client uses SMTP to communicate with your email provider’s server. The SMTP server then routes the email to the recipient’s email provider, where it can be retrieved by the recipient.
Q.2 (a) Describe OSI reference model with a neat diagram. ( repeated from dec check answer above )
Q2 (b) Explain different framing methods.
https://www.doubtly.in/10867/explain-different-framing-methods
Q.3 (a) Explain different types of guided transmission media in detail. ( repeated from dec check answer above )
Q3 (b) Explain sliding window protocol using selective repeat technique. ( repeated from dec check answer above )
Q.4 (a) Explain Link State Routing with suitable example.
https://www.doubtly.in/10871/explain-link-state-routing-with-suitable-example
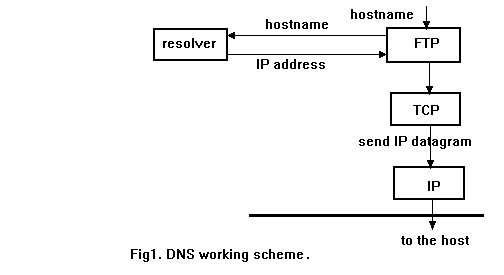
Q4 (b) What is need of DNS and explain how DNS works?
DNS, or Domain Name System, is a fundamental component of the internet that translates human-readable domain names into IP addresses, allowing users to access websites and other resources using familiar names rather than numeric IP addresses.
The need for DNS arises from the fact that computers on the internet communicate with each other using IP addresses, which are numerical identifiers associated with each device. However, remembering and using IP addresses for every website or online resource would be impractical for users. This is where DNS comes in, providing a hierarchical and distributed system to map domain names to IP addresses.
Here’s a brief explanation of how DNS works:
- User Enters a Domain Name: When a user enters a domain name (e.g., www.example.com) into their web browser, a request is initiated to resolve that domain to an IP address.
- Local DNS Resolver: The user’s device first checks its local DNS resolver cache to see if it already has the IP address for the requested domain. If the information is not found or has expired, the resolver proceeds to the next step.
- Recursive DNS Server: The local DNS resolver queries a recursive DNS server. Recursive DNS servers are responsible for resolving domain names by interacting with other DNS servers to find the correct IP address.
- Root DNS Server: If the recursive DNS server doesn’t have the IP address information, it contacts one of the 13 root DNS servers. These servers hold information about the top-level domain (TLD) name servers.
- TLD Name Server: The root DNS server directs the recursive server to the TLD name server responsible for the specific domain extension (e.g., .com, .org). The TLD name server stores information about the authoritative name servers for the requested domain.
- Authoritative DNS Server: The TLD name server then directs the recursive server to the authoritative DNS server for the requested domain. This server holds the specific IP address associated with the domain.
- IP Address Resolution: The authoritative DNS server provides the IP address to the recursive server, which, in turn, stores the information in its cache and returns the IP address to the user’s device.
- Accessing the Website: Now armed with the IP address, the user’s device can establish a connection to the desired web server, and the requested web page is delivered to the user’s browser.
DNS operates in the background, making internet usage more user-friendly by allowing people to access websites using easy-to-remember domain names while the system efficiently translates those names into the corresponding IP addresses required for actual communication between devices on the internet.
Q.5 (a) Explain IPv4 header format in detail.
https://www.doubtly.in/10875/explain-ipv4-header-format-in-detail
Q5 (b) Explain Three Way Handshake Technique in TCP.
https://www.doubtly.in/10758/explain-three-ways-handshake-technique-in-tcp?show=10758#q10758
Q.6 (a) Explain leaky bucket algorithm and compare it with token bucket algorithm. ( Answer required )
https://www.doubtly.in/10870/explain-leaky-bucket-algorithm-and-compare-with-token-bucket-algorithm
Q6 (b) Write short notes on: (i) TCP Timers (ii) HTTP
(i) TCP Timers:
a. Time-Out Timer:
- The Time-Out Timer in TCP (Transmission Control Protocol) is used to manage the retransmission of data in case of lost or delayed packets.
- When a sender transmits a segment, it starts the timer. If an acknowledgment is not received before the timer expires, the sender assumes that the segment was lost and retransmits it.
b. Time Wait Timer:
- The Time Wait Timer is associated with the TCP connection termination process.
- After a connection is closed, the socket pair enters the TIME_WAIT state to ensure that any delayed packets are not misinterpreted in subsequent connections.
- The Time Wait Timer ensures that the TIME_WAIT state does not last indefinitely, preventing resource exhaustion.
c. Keep Alive Timer:
- The Keep Alive Timer is designed to prevent idle connections from being terminated by routers or firewalls.
- Periodic keep-alive messages are sent over the connection, and if no response is received within a specified time (determined by the timer), the connection may be considered as idle and subject to termination.
d. Persistent Timer:
- The Persistent Timer is related to the handling of the TCP Persist Timer event.
- It is used to prevent a sender from being stuck in a transmit window when the receiver’s window size is zero. The Persistent Timer triggers the retransmission of small segments to probe for changes in the receiver’s window size.
(ii) HTTP (Hypertext Transfer Protocol):
- Overview:
- HTTP is a protocol for communication on the World Wide Web.
- It is the foundation for data communication on the web and facilitates the transfer of hypertext documents, which can contain text, images, multimedia, etc.
- Key Features:
- Stateless Protocol: Each request from a client to a server is independent, and the server doesn’t retain information about the client’s state between requests.
- Request-Response Model: Clients (e.g., browsers) send HTTP requests to servers, and servers respond with the requested information.
- Uniform Resource Identifiers (URIs): Used to identify resources on the web, such as web pages or images.
- Versions:
- HTTP/1.0: The initial version.
- HTTP/1.1: Improved performance through persistent connections, caching, and other enhancements.
- HTTP/2: Major improvements in speed and efficiency, with features like multiplexing and header compression.
- Methods:
- GET: Retrieve data from the server.
- POST: Send data to be processed to a specified resource.
- PUT: Update a resource on the server.
- DELETE: Request the removal of a resource.
- Status Codes:
- Examples include 200 OK (successful), 404 Not Found (resource not found), and 500 Internal Server Error (server error).
- Headers:
- Used for passing additional information in both requests and responses.
- Examples include “Content-Type” indicating the type of data being sent and “User-Agent” identifying the client application.
- Connection Types:
- Persistent (Keep-Alive): Multiple requests and responses can be sent over a single connection, reducing latency.
- Non-Persistent: A new connection is established for each request-response pair.
- Security:
- HTTPS (HTTP Secure) is a secure version of HTTP that uses encryption (SSL/TLS) to protect data during transmission.
