CSS Question Paper solution Dec 2023
Table of Contents
Note:
1. Question 1 is compulsory.
2. Attempt any 3 questions out of the remaining questions.
Q1. Attempt any Four. ( CSS Question Paper solution Dec 2023 )
a. Explain the different modes of block ciphers. [repeated]
Block cipher is an encryption algorithm that takes a fixed size of input say b bits and produces a ciphertext of b bits again. If the input is larger than b bits it can be divided further. For different applications and uses, there are several modes of operations for a block cipher.
Electronic Code Book (ECB) –
Electronic code book is the easiest block cipher mode of functioning. It is easier because of direct encryption of each block of input plaintext and output is in form of blocks of encrypted ciphertext. Generally, if a message is larger than b bits in size, it can be broken down into a bunch of blocks and the procedure is repeated.
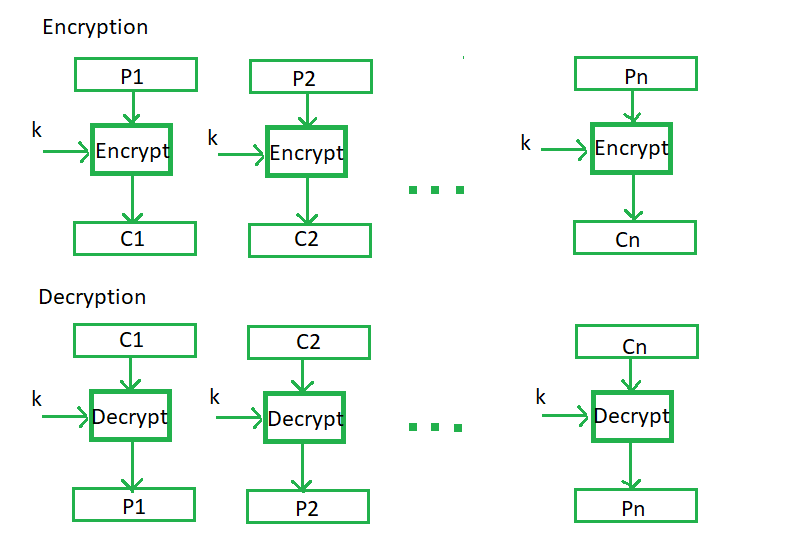
Cipher Block Chaining –
Cipher block chaining or CBC is an advancement made on ECB since ECB compromises some security requirements. In CBC, the previous cipher block is given as input to the next encryption algorithm after XOR with the original plaintext block. In a nutshell here, a cipher block is produced by encrypting an XOR output of the previous cipher block and present plaintext block.
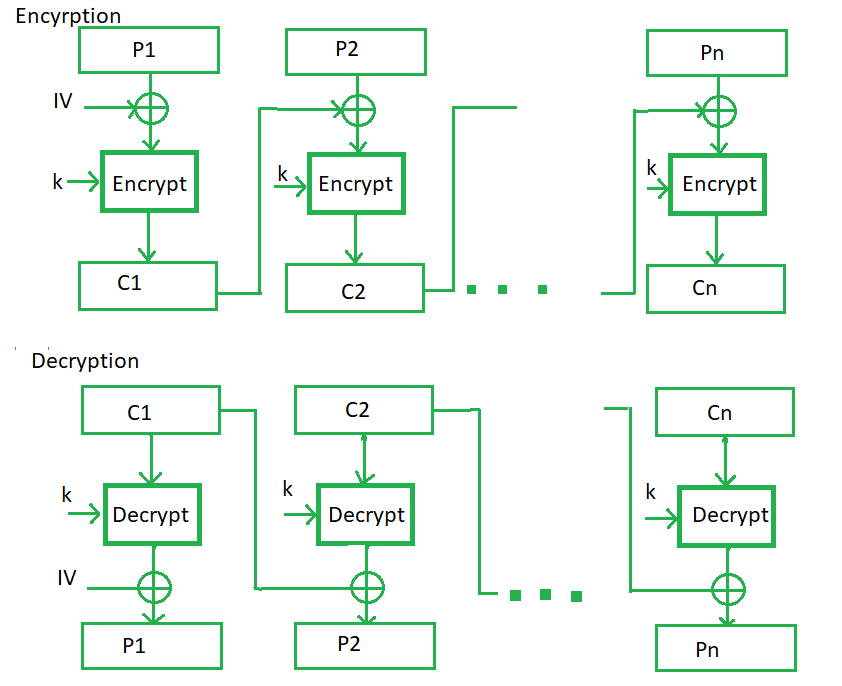
Cipher Feedback Mode (CFB) –
In this mode the cipher is given as feedback to the next block of encryption with some new specifications: first, an initial vector IV is used for first encryption and output bits are divided as a set of s and b-s bits.The left-hand side s bits are selected along with plaintext bits to which an XOR operation is applied. The result is given as input to a shift register having b-s bits to lhs,s bits to rhs and the process continues. The encryption and decryption process for the same is shown below, both of them use encryption algorithms.
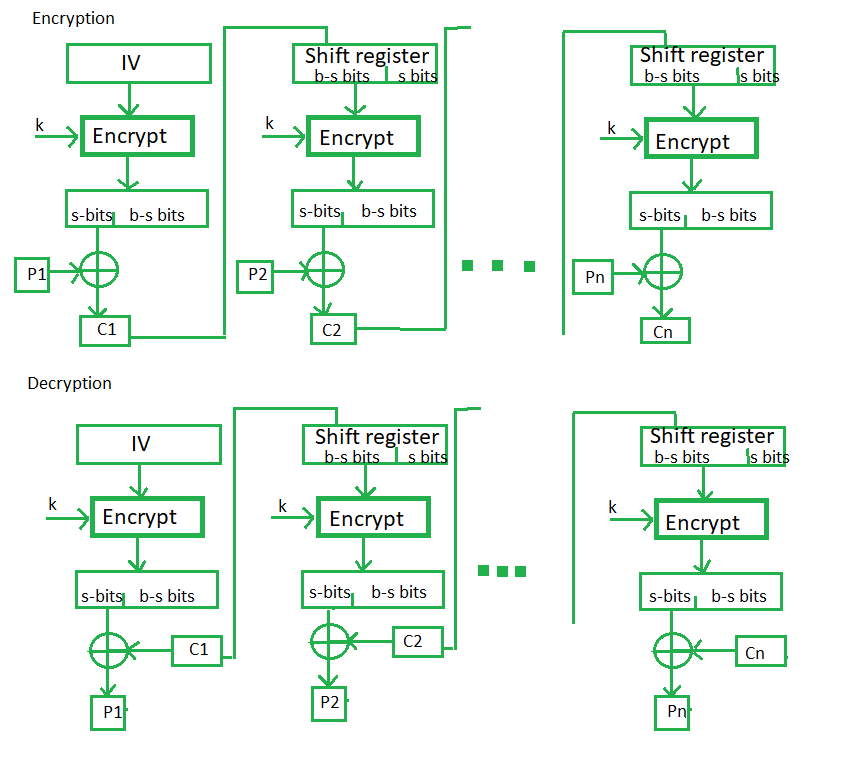
Output Feedback Mode –
The output feedback mode follows nearly the same process as the Cipher Feedback mode except that it sends the encrypted output as feedback instead of the actual cipher which is XOR output. In this output feedback mode, all bits of the block are sent instead of sending selected s bits. The Output Feedback mode of block cipher holds great resistance towards bit transmission errors. It also decreases the dependency or relationship of the cipher on the plaintext.
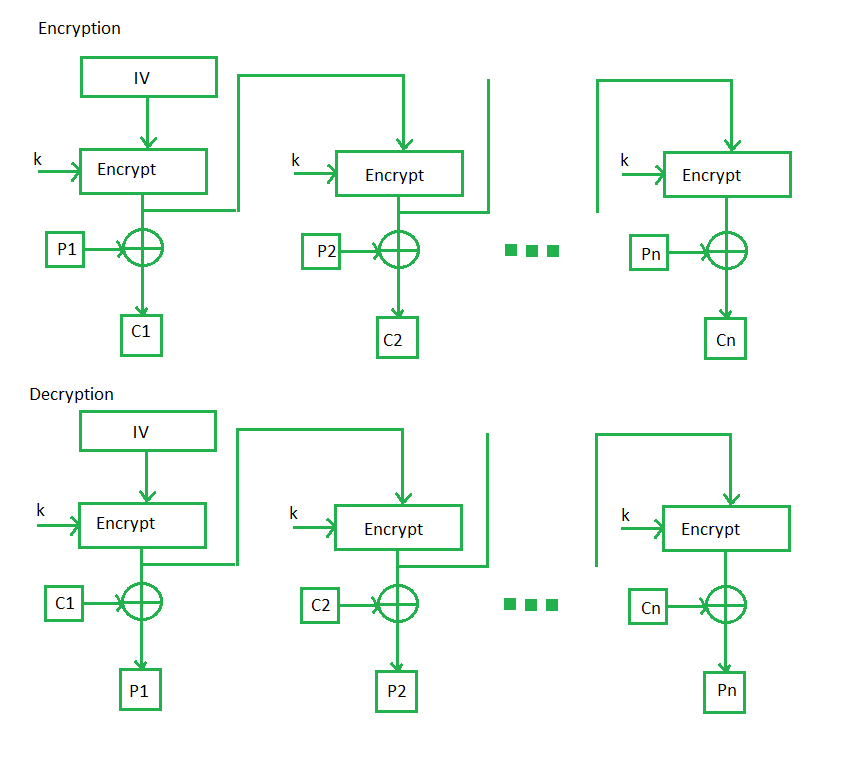
Counter Mode –
The Counter Mode or CTR is a simple counter-based block cipher implementation. Every time a counter-initiated value is encrypted and given as input to XOR with plaintext which results in ciphertext block. The CTR mode is independent of feedback use and thus can be implemented in parallel.
Its simple implementation is shown below:
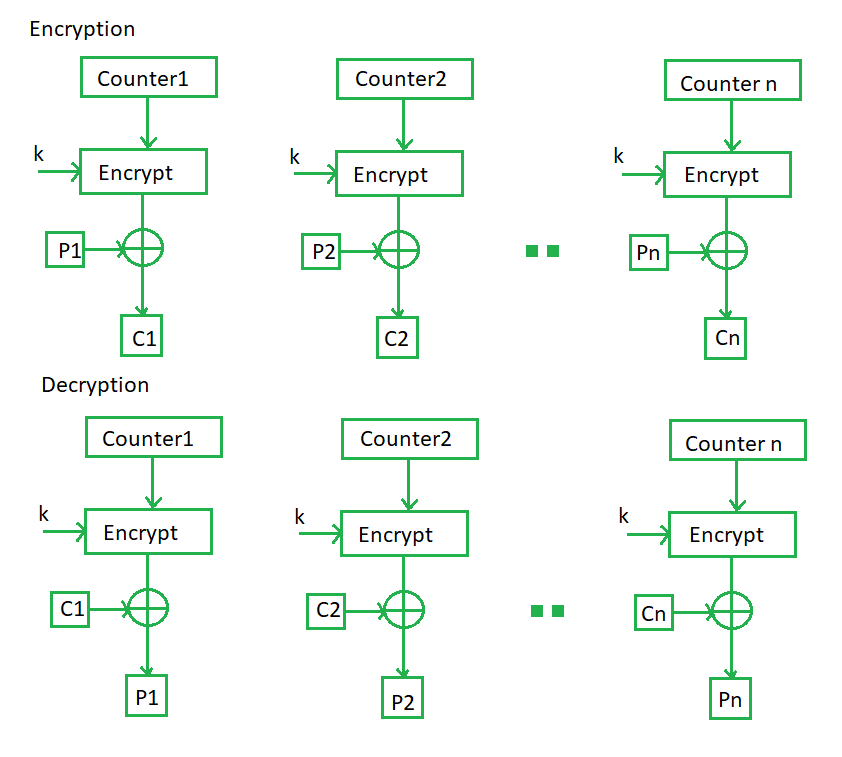
Src : https://www.geeksforgeeks.org/block-cipher-modes-of-operation/
b. List with examples the different mechanisms to achieve security.
Types of Security Mechanism are :
- Encipherment :
This security mechanism deals with hiding and covering of data which helps data to become confidential. It is achieved by applying mathematical calculations or algorithms which reconstruct information into not readable form. It is achieved by two famous techniques named Cryptography and Encipherment. Level of data encryption is dependent on the algorithm used for encipherment. - Access Control :
This mechanism is used to stop unattended access to data which you are sending. It can be achieved by various techniques such as applying passwords, using firewall, or just by adding PIN to data. - Notarization :
This security mechanism involves use of trusted third party in communication. It acts as mediator between sender and receiver so that if any chance of conflict is reduced. This mediator keeps record of requests made by sender to receiver for later denied. - Data Integrity :
This security mechanism is used by appending value to data to which is created by data itself. It is similar to sending packet of information known to both sending and receiving parties and checked before and after data is received. When this packet or data which is appended is checked and is the same while sending and receiving data integrity is maintained. - Authentication exchange :
This security mechanism deals with identity to be known in communication. This is achieved at the TCP/IP layer where two-way handshaking mechanism is used to ensure data is sent or not - Bit stuffing :
This security mechanism is used to add some extra bits into data which is being transmitted. It helps data to be checked at the receiving end and is achieved by Even parity or Odd Parity. - Digital Signature :
This security mechanism is achieved by adding digital data that is not visible to eyes. It is form of electronic signature which is added by sender which is checked by receiver electronically. This mechanism is used to preserve data which is not more confidential but sender’s identity is to be notified.
c. Differentiate MD5 and SHA-1 algorithms. [repeated]
d. List and explain security requirements of database.
Answer here : https://www.doubtly.in/q/list-explain-security-requirements-database/
e. Explain phishing and list different types of phishing techniques.
Phishing is a type of cyber attack where attackers use deceptive tactics to trick individuals into revealing sensitive information such as login credentials, personal information, or financial data. Phishing attacks often involve impersonating trusted entities, such as legitimate organizations or individuals, to manipulate victims into taking actions that benefit the attackers.
Types of phishing techniques:
- Email Phishing: Attackers send fraudulent emails posing as legitimate organizations or individuals, often with urgent or enticing messages, to trick recipients into clicking on malicious links or downloading attachments that contain malware. Email phishing is one of the most prevalent and widely known types of phishing.
- Spear Phishing: Spear phishing is a targeted form of phishing where attackers customize their fraudulent messages for specific individuals or organizations. The emails often contain personalized information obtained through reconnaissance, making them more convincing and difficult to detect.
- Clone Phishing: In clone phishing, attackers create replica emails that appear to be legitimate copies of previously received emails from trusted sources. The cloned emails typically contain malicious links or attachments, exploiting the recipient’s familiarity with the original email to increase the likelihood of success.
- Vishing (Voice Phishing): Vishing involves using voice communication, such as phone calls or VoIP (Voice over Internet Protocol), to deceive victims into divulging sensitive information. Attackers may impersonate legitimate entities, such as bank representatives or tech support personnel, to trick victims into providing account credentials or financial information over the phone.
- SMiShing (SMS Phishing): SMiShing refers to phishing attacks conducted via SMS (Short Message Service) or text messages. Attackers send fraudulent text messages containing malicious links or prompts to call a phone number, often impersonating legitimate organizations or claiming that the recipient has won a prize to lure victims into disclosing personal information or installing malware.
- Pharming: Pharming attacks involve redirecting victims to fraudulent websites or web pages without their knowledge. Attackers manipulate DNS (Domain Name System) or compromise routers and DNS servers to redirect users from legitimate websites to malicious ones, where they may be prompted to enter sensitive information.
- Man-in-the-Middle (MITM) Attacks: In MITM attacks, attackers intercept communication between the victim and a legitimate entity, such as a website or email server, to eavesdrop on or manipulate the exchange of information. Attackers may capture login credentials, financial data, or other sensitive information transmitted between the victim and the legiti
Q2 a. User A and B want to use RSA to communicate securely. A chooses public key as (7, 119) and B chooses public key as (13, 221). Calculate their private keys. A wishes to send message m = 10 to B. Produce the ciphertext. Formulate the key using which A encrypt the message “m” if A need to authenticate itself to B.
Answer here : https://www.doubtly.in/q/user-rsa-communicate-securely/
Q2 b. Explain memory and address protection in detail. Write a note on file protection. 10
THIS ANSWER IS AN CHATGPT GENERATED ANSWER
Memory and Address Protection:
- Memory Protection: Memory protection is a mechanism to control access to memory locations in a computer’s memory. It prevents a process from accessing memory that has not been allocated to it or from accessing memory allocated to another process. This prevents accidental or malicious interference between processes and enhances system stability and security.
- Address Protection: Address protection is a subset of memory protection. It involves techniques to ensure that memory addresses accessed by a process are valid and within the boundaries of the allocated memory for that process. This prevents buffer overflows, pointer manipulation attacks, and other vulnerabilities that can be exploited by attackers to gain unauthorized access to system resources.
- Techniques used for Memory and Address Protection:
- Memory Segmentation: Memory segmentation divides memory into segments and assigns different segments to different processes. Each segment has its own access rights, such as read, write, and execute permissions.
- Memory Paging: Memory paging divides memory into fixed-size blocks called pages. Each page can be individually protected with access permissions. It also enables virtual memory management, allowing the operating system to manage memory more efficiently.
- Memory Protection Units (MPUs) and Memory Management Units (MMUs): Hardware components like MPUs and MMUs are used to enforce memory protection at the hardware level. They can restrict access to memory based on permissions set by the operating system.
File Protection:
File protection involves controlling access to files stored on a computer’s file system. It ensures that only authorized users or processes can read, write, or execute files, thereby safeguarding sensitive data and system integrity.
- Access Control Lists (ACLs): ACLs are lists of permissions attached to files or directories. They specify which users or groups have access to the file and what actions they can perform (e.g., read, write, execute). ACLs provide granular control over file access, allowing administrators to define precise access policies.
- File Ownership: Each file in a file system is associated with an owner and a group. File ownership determines who has the authority to modify permissions and access control settings for the file. Only the owner or a privileged user (e.g., the system administrator) can change ownership or modify permissions.
- File System Permissions: File systems support permissions that define what actions can be performed on a file by different categories of users: owner, group, and others. These permissions typically include read, write, and execute permissions. By setting appropriate permissions, administrators can control who can view, modify, or execute files.
- Encryption: Encryption is another layer of file protection that involves encoding the contents of a file using encryption algorithms. Encrypted files can only be accessed by users with the decryption key, ensuring confidentiality even if unauthorized users gain access to the file.
